Incremental Saving Attack (ISA)
This class of attack relies on the PDF feature incremental saving (incremental update). The idea of the attack is to make an incremental saving on the document by redefining the document's structure.
In a legitimate use-case, incremental saving is used, for example, to add annotations to a PDF. The annotations itself are incrementally saved after the original content of the PDF as a new PDF body. Incremental saving is also used for signing a PDF: the signature object is simply appended to the original file content.
The idea of ISA is the following:
The attacker takes a signed PDF. He adds new content (pages, annotations, etc.) and stores them at the end of the file using incremental saving. This is basically not an attack, but a feature of PDF. A vulnerability appears once the signature validation logic does not notice that the file content has been updated, i.e., that new, unsigned content has been added to the file. To achieve this behavior, we identified multiple variants of the attacks as shown below:
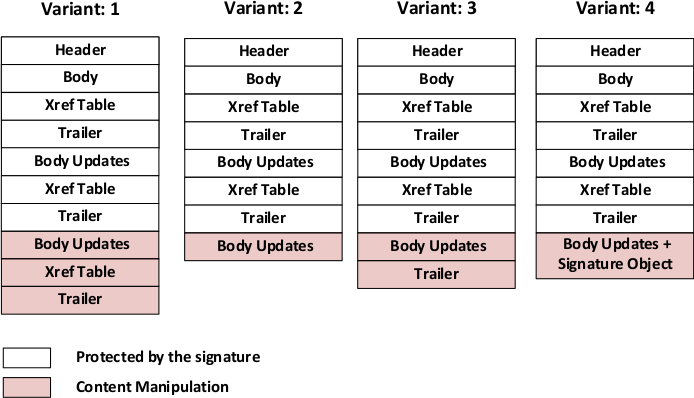
Please note that Variant 1 itself is not a real attack vector. It is the intended file structure of a signed PDF that has been updated using incremental saving. Variants 2-4 are not compliant to the PDF specification, e.g., they do not define a new xref or trailer, but PDF applications are error tolerant and display the content anyway.
In total, the ISA attack is successful if:
- the new Content (Body Updates) is shown and
- the application does not notice that the document has been modified or updated.